TL;DR: I scanned 173 nominees across 10 categories and, after deduplication, analyzed 137 unique domains using client-side evidence captured before consent. Only 22 nominees land in a low-risk range of 0-4 pre-consent findings, which means 151 out of 173 are still non-compliant by a conservative measure - 87.28%. The headline is not which vendor is popular; it’s that “consent before tracking” is still not the default operating mode in Danish e-commerce. The good news is that a meaningful group now shows zero or near-zero pre-consent evidence, proving correct gating is possible in real commerce stacks.
Progress, but still systematic data abuse before consent
This is the 4th year I’m auditing the top nominees in the Danish E-Commerce Awards. The reason I keep doing it is simple: e-commerce is where “growth” and “compliance” collide in real life - and it’s also where the gap between what companies claim and what their sites actually do becomes measurable.
This is not a niche compliance debate. This award is a benchmark for what Denmark calls “best practice” in e-commerce. That’s why it matters whether the winners are building trust - or quietly bypassing it.
This is also why the organizer matters. When Dansk Erhverv - Digital Handel positions these nominees as “the best of Danish e-commerce”, it becomes a benchmark for what the industry normalizes - including in a time where Denmark is debating digital independence and trust.
This year I want to highlight two things at the same time. First, we are finally seeing a meaningful group of nominees with zero or near-zero pre-consent evidence. Second, the broader dataset still shows that the default operating mode across the industry is to load tracking before consent.
“Only 22 out of 173 nominees land in a low-risk range. The remaining 87.28% still leak before consent.”
What the study measures
The award list contains 173 nominees across 10 categories. Because some nominees appear in multiple categories, the list contains duplicates. After deduplication, the dataset covers 137 unique website domains.
Unless otherwise stated, scans were performed using the AesirX Privacy Scanner (hosted in Germany), based on the EDPS Inspection Tool / Website Evidence Collector engine. For automated processing, 172 scan result URLs were generated and deduplicated to 136 unique domains, and one domain (henosia.com) is included through manual HAR-based handling due to an application error. On Henosia, the HAR shows one first-party analytics beacon (PostHog-ingest style) and zero cookies.
The analysis is limited to client-side evidence captured by scanner/HAR: network requests classified as beacons and cookies set or observed before a valid consent signal. Sites are not assessed for server-side tracking, proxying, masking, or other circumvention techniques. Actual data collection may therefore exceed what is reflected in these results.

The legal foundation in Denmark
The compliance baseline in Denmark is not a grey-zone “risk assessment” exercise. It is governed by two different legal pillars and two different authorities.
GDPR is implemented via Databeskyttelsesloven and enforced by Datatilsynet. If you process personal data for marketing measurement and tracking, you need a lawful basis that matches reality, and if you rely on consent, that consent must be freely given, specific, informed, unambiguous, and withdrawable.
The terminal equipment rule is ePrivacy Directive Article 5(3), implemented in Denmark via cookiebekendtgørelsen and governed by Digitaliseringsstyrelsen. This rule is binary: storing or accessing information on the user’s device requires prior consent unless it is strictly necessary for the service the user explicitly requested.
That “strictly necessary” exception is narrow. It is not a blanket justification for attribution, marketing optimization, telemetry, profiling, enrichment, or vendor-side measurement. If tracking beacons and/or non-essential cookies are observed before a valid consent signal, the implementation fails the “consent before access/storage” requirement under cookiebekendtgørelsen, and it will often also fail GDPR requirements for valid consent.
In practice, GDPR asks whether your processing is lawful; ePrivacy Directive 5(3) asks the simpler question first: did you access the device for non-essential purposes before consent - yes or no.
Read the full joint guidelines on cookies and tracking technologies from Datatilsynet and Digitaliseringsstyrelsen.
The headline finding: 87.28% still non-compliant
Here is the conservative classification that matters for any serious discussion.
Only 22 out of 173 nominees score in a low-risk range. Conservatively, 0-4 findings is a low-risk range and a reasonable proxy for likely compliance in this dataset.
The remaining 151 nominations are classified as non-compliant under cookiebekendtgørelsen (ePrivacy Directive Article 5(3)) in Denmark and/or Databeskyttelsesloven (GDPR), because they trigger tracking evidence prior to a valid consent signal.
This is the core narrative point. Not “which vendor is most common”. Not “which CMP is trending”. The baseline question is: does tracking start before consent - yes or no.

Why this keeps happening in e-commerce
The recurring cause is not ignorance of the law - it is the way e-commerce stacks are assembled. Templates ship with tag managers and marketing widgets enabled by default, teams inherit “measurement-first” setups from agencies, and vendor stacks are increasingly bundled so telemetry, attribution, personalization, reviews, and email marketing are fused together. The result is predictable: tracking initializes first, and consent logic is asked to retroactively justify what already happened.
The law does not allow retroactive gating. If the first network requests and device identifiers appear before consent, the implementation is structurally non-compliant - even if the banner looks polished.
What still loads before consent
This is where the technical reality becomes uncomfortable, because it shows how the modern marketing stack behaves by default.
1) Tag infrastructure and tracking endpoints still fire pre-consent
In the deduplicated dataset of 137 unique domains, the Top Beacon Hosts table counts how many unique domains triggered at least one pre-consent request to each host and how frequently those hosts appear across the dataset.
A major signal remains that Google Tag Manager loads pre-consent on 92 out of 137 domains, which is 67.15%. That is not a “minor configuration edge case”. It is the default operating mode.
“If your first request is a tag manager, your consent logic is already chasing a train that left the station.”
![]()
In other words, the industry’s default architecture is still “tag manager first, consent later” - which is backwards under ePrivacy Directive 5(3).
2) Tracking cookies are still being set pre-consent
The Top Cookies table counts cookie families observed across unique domains, filters out obvious platform/essential cookies and common consent cookies, and focuses on tracking identifiers that appear prior to consent.
That matters because ePrivacy Directive 5(3) is not “cookie theatre”. It’s device access. If tracking cookies are set before consent, the implementation fails the baseline.
“If tracking cookies are set pre-consent, the compliance discussion is already over.”
![]()
These identifiers are not “technical necessity”. They are marketing infrastructure, and when they appear pre-consent the implementation fails the baseline regardless of what the banner claims.
3) The consent layer is often part of the leak
This point is easy to misunderstand, so I’ll state it precisely.
The Top CMP table does not measure “CMP presence”. It measures pre-consent third-party calls to CMP-provider infrastructure that were classified as beacons in the export. In the deduplicated dataset (N=137 domains, including Henosia via HAR), at least one of the Top CMP providers was observed loading pre-consent on 97 out of 137 domains, which is 70.80%.
If a consent vendor processes data or accesses terminal equipment prior to consent for vendor purposes, such as telemetry, geo-IP lookups, or pixel trackers, that is not “technical necessity” on behalf of the visitor under GDPR and ePrivacy Directive 5(3). The consent mechanism becomes part of the non-compliant data flow.
“A consent layer that phones home before consent is not a gate. It’s part of the tracking.”
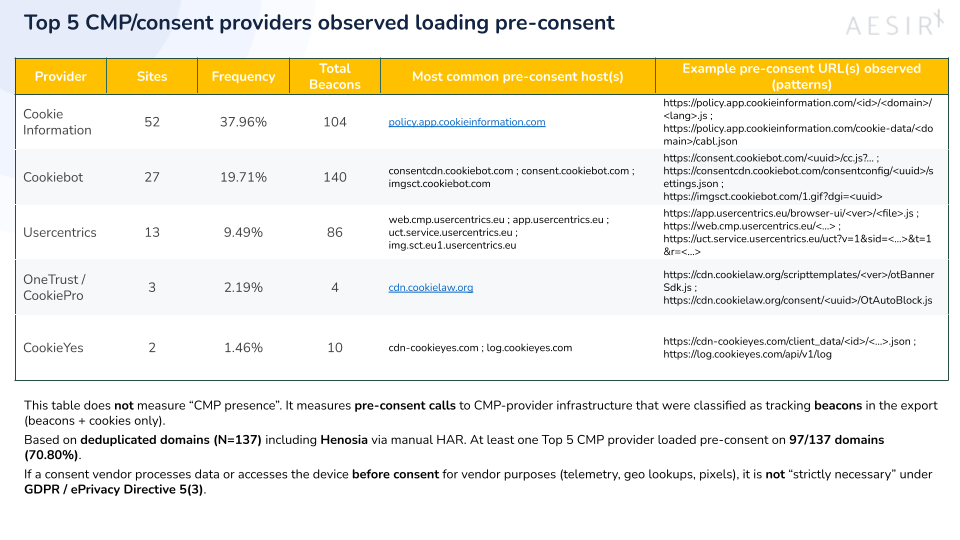
A consent layer that triggers vendor-side processing pre-consent turns compliance into theatre, because the “gate” is already exchanging data before the visitor decides.
A growing part of this problem is bundling. Vendors increasingly ship CMP, analytics, marketing automation, widgets, and CDNs as one stack. That makes implementation easier, but it also blurs purposes and recipients, and it creates pressure to treat vendor telemetry as “necessary”. The strict necessity test is about what the visitor requested - not what the vendor needs for attribution, invoicing, enrichment, or product analytics.
Worst and best: the spread tells the truth
I rank domains by total observed pre-consent activity (beacons + cookies). The purpose is not drama. The purpose is to show the distance between “we can’t” and “we did”.
Top 10 Non-Compliant
This list ranks the highest observed pre-consent totals. The unit is unique nominee domains in the final deduped dataset (n=137), and totals are calculated from client-side evidence observed before consent.

These are not outliers. They are what happens when the stack is allowed to initialize marketing infrastructure before consent.
Top 10 Best (lowest observed)
This list ranks the lowest observed totals. “0” does not prove compliance. It means no tracking-classified beacons or tracking cookie identifiers were observed pre-consent in the captured client-side evidence, and server-side/proxy/masking was not assessed.
This matters because it proves the industry excuse is wrong. It is possible to build an e-commerce stack that does not leak by default.

These are the proof cases. They show that you can run serious commerce without pre-consent leakage, if you gate properly and keep telemetry in check.
A note on the “Best e-commerce case” nominees
For the Best e-commerce case nominees, the scanned domain reflects the customer/case implementation presented. The scan is used as an indicator of the solution’s ability to support compliance with Danish and European requirements, including Databeskyttelsesloven (GDPR) and cookiebekendtgørelsen (ePrivacy Directive Article 5(3)).
That means the scan is not just a comment on a brand. It is also a signal about the implementation model being showcased as “best practice”.
Banners don’t create compliance - architecture does
The e-commerce industry needs to stop treating this as a copywriting problem and start treating it as an engineering property.
The simplest compliance test in Denmark is still the most powerful: does your site store or access tracking identifiers on the device or call tracking endpoints before consent - yes or no. That is cookiebekendtgørelsen implementing ePrivacy Directive 5(3), and it is governed by Digitaliseringsstyrelsen. If you process personal data for tracking and rely on consent that is not freely given, informed, and specific, that is GDPR via Databeskyttelsesloven, governed by Datatilsynet.
This year’s dataset shows two truths at once. A small group proves compliant gating is feasible. The majority proves that the default is still systematic pre-consent tracking.
And if we don’t call that what it is, the industry will keep polishing banners while the data flows remain unchanged.
And that is exactly why the award benchmark itself has to be part of the discussion.
Digital independence vs data doping: the contradiction in plain numbers
Denmark is having a serious debate about digital independence from US BigTech. That is exactly why it’s hard to read this dataset without calling out the hypocrisy: Google Tag Manager loads pre-consent on 67.15% of top nominees. That is not “digital leadership”. That is a structural dependency - and it’s incompatible with the story Denmark tells itself about taking control of its digital future.
I’m not asking an award show to act as a regulator. I’m asking an industry organisation to stop treating “growth at any cost” as excellence when it conflicts with Danish law and public trust. If an awards benchmark ignores GDPR and ePrivacy Directive 5(3) year after year, it doesn’t just reflect the market - it trains the market.
This is a question for Dansk Erhverv - Digital Handel and for Brian Mikkelsen: do we want Danish digital leadership to mean sovereignty and trust - or just better optimization on top of illegal tracking?
“If 67.15% of ‘top’ nominees load GTM before consent, the award isn’t measuring excellence - it’s measuring how well data doping performs..”
If Denmark wants digital leadership, we must stop awarding stacks that treat consent as a decorative layer on top of default surveillance.
Full findings and category tables
I’m publishing the full results as a PDF carousel so you can verify everything without taking my word for it.
The carousel includes the complete Top 20 nominee tables for all 10 categories, plus the cross-category summary tables: Top 10 Beacons, Top 10 Cookies, Top 5 CMPs, Top 10 Non-Compliant, and Top 10 Compliant / Lowest observed.
Use it like a reference deck: open your category, find the nominee, and you’ll see immediately whether tracking starts before consent.
What you can do next
If you want to check your own site, start with the same method this study uses: measure what loads before consent. Run your domain through the AesirX Privacy Scanner and review the client-side evidence (beacons and cookies) that appears before a valid consent signal.
If the scanner shows pre-consent tracking evidence, you already have the diagnosis: consent gating and configuration are broken under ePrivacy Directive 5(3), and the GDPR consent story will often also fail because the processing begins before any valid choice exists.
Start there. If your pre-consent findings are 0-4 you’re likely in a good place. If not, you have a concrete engineering problem to fix.
If you want a prioritized remediation plan you can hand to developers or an agency, the Technical Privacy Review converts evidence into fixes - what leaks, why it leaks, and what to change first.
Ronni K. Gothard Christiansen
Technical Privacy Engineer & CEO @ AesirX.io




