Data privacy is not only a legal obligation, but also a competitive advantage for any organization that collects, processes, or stores personal data. However, data privacy compliance is not a one-time event, but a continuous process that requires constant monitoring, evaluation, and improvement.
To help organizations comply with data privacy laws and regulations, we have developed 5 key elements, or pillars of data privacy accountability and compliance, which are a set of guidelines and best practices that can help businesses achieve global data privacy compliance. They are based on GDPR principles, requirements, and obligations. (GDPR is one of the most important and comprehensive data privacy regulations in the world).

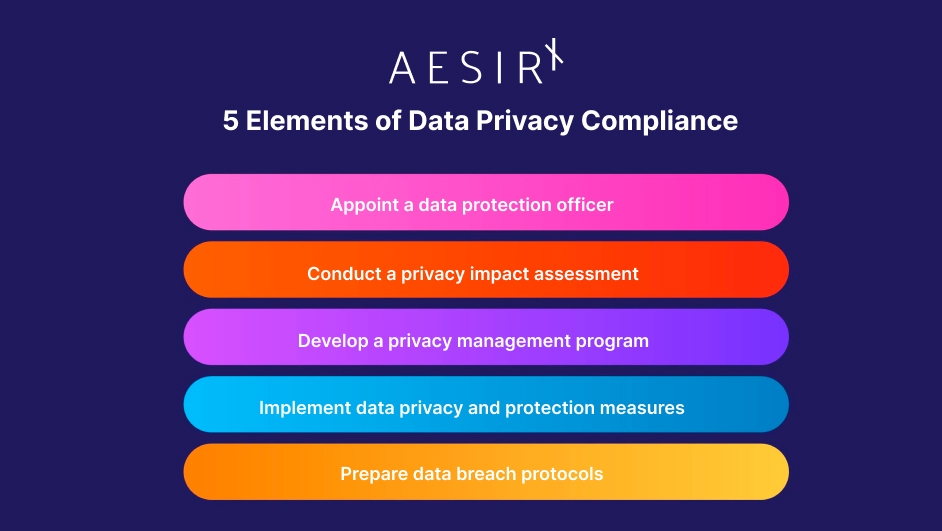
Understanding the 5 Elements of Data Privacy Compliance
Data privacy is about protecting personal information from unauthorized access or misuse. Businesses in the EU and other countries that process personal data of EU citizens must implement measures to ensure the security of personal data handled in accordance with the GDPR. The 5 elements of data privacy accountability and compliance include:
1. Appoint a Data Protection Officer (DPO)
A DPO is a person who is responsible for overseeing the data privacy and protection policies and practices of the organization. The DPO should have the necessary knowledge, skills, and authority to handle tasks like privacy assessments, creating privacy programs, enforcing data security, addressing breaches, and communicating with data subjects and regulators.
2. Conduct a Privacy Impact Assessment (PIA)
A PIA is a process that helps identify and evaluate the risks and impacts of data processing activities on the privacy and rights of data subjects. A PIA should be conducted before, during, and after any data processing, like collecting, storing, sharing, or deleting personal data.
The assessment should also cover legal, technical, organizational, and ethical aspects, offering recommendations to minimize or eliminate identified risks and impacts.
3. Develop a Privacy Management Program (PMP)
A PMP is a document that outlines an organization's data privacy and protection policies and procedures. It should include:
- A privacy statement or notice to inform data subjects about the purpose, scope, and methods of data processing.
- A privacy manual as a guide for ensuring data privacy compliance.
- A data governance framework defining roles, responsibilities, and accountabilities of data processors and controllers.
- A data inventory listing and categorizing the personal data processed by the organization.
- A data retention and disposal policy specifying the period and manner of keeping and deleting personal data.
- A data sharing policy regulating the transfer and disclosure of personal data to third parties.
4. Implement Data Privacy and Protection Measures
Data privacy and protection measures, including online security measures and data privacy technology, are the technical and organizational safeguards designed to prevent or reduce the occurrence and impact of data breaches and other privacy incidents. These measures should follow principles like data minimization, purpose limitation, accuracy, storage limitation, integrity, confidentiality, and accountability.
Examples of such measures include encryption, pseudonymization, anonymization, access control, authentication, authorization, and other advanced technologies ensuring online security.
5. Prepare Data Breach Protocols
are the plans and procedures that the organization follows in the event of a data breach or other data privacy incident. Data breach protocols should include the following steps: detection, containment, analysis, notification, recovery, and evaluation. Data breach protocols should also comply with the reporting and notification requirements of the relevant data privacy laws and regulators.
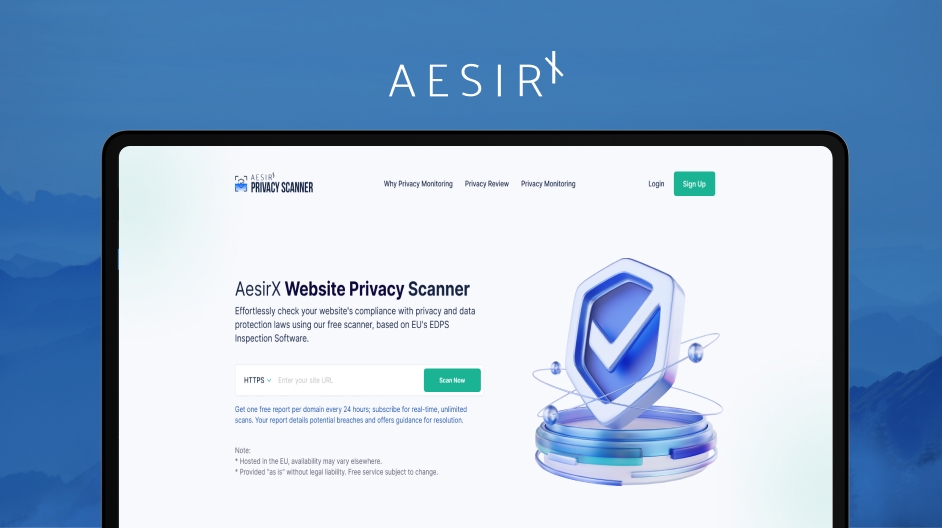
AesirX Privacy Scanner: A Free Tool for Data Privacy Assessment
One of the challenges of data privacy compliance is to monitor and assess the compliance status of the websites and online platforms that the organization owns or uses. Websites and online platforms are often the main sources and channels of personal data collection and processing, and therefore, they should comply with the data privacy laws and regulations that apply to them.
AesirX Privacy Scanner is a free tool that helps scan and check websites for data protection and privacy compliance. The scanner is based on the EDPS Inspection Software developed by the European Union. The scanner can detect and report the following issues:
- Website's structure
- Online security measures (HTTPS/SSL)
- Social media presence
- Traffic analysis, persistent data (cookies and local storage)
- Potential tracking elements like web beacons
The scanner can also provide a detailed report with links to the laws and regulations violated, along with information on how to fix the issues.
To use the scanner, simply enter the URL of the website you want to scan and click the "Scan Now" button. You can immediately view the scan results and a report. You can also read the full report in PDF format by downloading it and sharing it with your customers, partners, and colleagues.
Regular Automated Scans for Continuous Compliance
AesirX Privacy Scanner can be used to automate data privacy compliance checks, serving as a stand-in for a comprehensive and ongoing privacy impact assessment. In addition to the free edition with manual scanning, AesirX Privacy Scanner now provides Daily, Weekly, Monthly, and Enterprise level scans, with detailed reports delivered to your email. (Learn More)
While most scanners on the market can only detect and report issues that are visible and accessible from the website, AesirX goes above and beyond. It can evaluate data processing activities that take place behind the scenes, such as data storage, sharing, and collection. However, the limitation of all data privacy compliance scanner tools is that users must address the issues based on the results and recommendations themselves. To ensure that privacy risks are identified and fully resolved, it is recommended that the organization conduct a full privacy impact assessment and develop a privacy management program with AesirX Privacy Compliance Review.
Enhanced Trust through Concordium Blockchain Integration
AesirX Privacy Scanner introduces a new era of trust with its integration of Concordium blockchain. This update focuses on increasing transparency, verification, and authentication, allowing users to easily demonstrate their adherence to privacy regulations.
The Concordium blockchain ensures that the time and date of each scanning report are securely and transparently recorded. This innovative feature provides clear and reliable confirmation of the report's authenticity.
By using blockchain technology, AesirX aims to instill maximum trust in the scanning process, assuring users and stakeholders that the results are not only accurate but also tamper-proof. This strategic integration reaffirms AesirX's commitment to elevating the standards of trust and reliability in the world of data privacy assessment.
AesirX Privacy Scanner is one of the innovative and privacy-focused solutions provided by AesirX, a technology ecosystem that includes Analytics, Single Sign On, Shield of Privacy, and other products and services that respect and protect customer data and privacy. AesirX aims to assist businesses in providing quality customer experiences while regulatory, cookie, and market changes affect the analytics and digital marketing landscape. AesirX also offers a free and open source strategy to businesses, as well as up to 25% affiliate commission to all partners.
Is your company privacy-compliant? Try AesirX Privacy Scanner to ensure you meet the 5 elements of data privacy accountability and compliance. See how it can help you achieve data privacy excellence.
Sources
1. https://www.compliancejunction.com/gdpr-compliance-checklist/




