TL;DR
Many ‘global’ sites hide consent outside Europe via geo-IP gating, adding new tracking and triggering ePrivacy Directive/GDPR risk before analytics even loads. Opt-in is the norm well beyond the EU - including Vietnam, South Korea, and India. Build for global consent, not just Europe.
Every week, I land on European websites and big-name e-commerce stores from Vietnam, where I reside. And every week the same thing happens: no consent banner, no controls, no transparency - because my IP address isn’t in Europe.
Is that ignorance or arrogance?
Either way, it’s a compliance and trust problem. “Cookie Consent as a Service” (CCaaS) vendors often geo-gate their banners to Europe only, even though many countries outside the EU/UK/EEA require opt-in consent for non-essential cookies and device access. Hiding the consent window for visitors in Vietnam, South Korea, India, Thailand, or Turkey isn’t just a UX decision - it can be unlawful. And yes, privacy matters in Ho Chi Minh City as much as it does in Hamburg.
What the law actually says
The EDPB’s 2024 guidance on ePrivacy Directive Article 5(3) is clear: if you store or access information on a user’s device (cookies, pixels, SDKs, local storage, fingerprinting - any tracker), you need prior, informed consent, unless the operation is strictly necessary to provide the service the user requested (e.g., login, cart, security). The CJEU confirmed in Planet49 that this prior-consent rule applies regardless of whether the data is personal - it’s about device access first, GDPR after.
Where GDPR bites as well: many CCaaS vendors first use the visitor’s IP address to decide whether to even show a banner. Under CJEU in Breyer (C-582/14), dynamic IP addresses are personal data, so sending IPs to a third-party CMP/CaaS for geo-lookup is personal data processing under GDPR. That means you must have:
- a lawful basis under Article 6 GDPR (and “legitimate interests” is hard to justify when geo-gating banners is not necessary for the user’s requested service),
- full transparency at collection time (Articles 5(1)(a) and 13: say why you send IPs to a CMP, who receives them, on what legal basis), and
- a compliant controller–processor contract (Article 28) - plus transfer safeguards if the vendor is outside the EEA. If those pieces aren’t in place, the IP sharing itself is non-compliant, before you’ve even looked at cookies.
It gets worse when vendors collect telemetry (page counts, events) to bill clients. That telemetry is not strictly necessary to deliver the page to the user, so ePrivacy Directive 5(3) still requires prior opt-in if telemetry touches the device (e.g., via pixels, tags). And if telemetry includes or links to personal data (IP, IDs, headers), GDPR also applies: you need a lawful basis, data-minimisation (Article 5(1)(c)), and the same Article 13/28 hygiene. Running these before consent typically breaks both the ePrivacy Directive and GDPR.
Bottom line:
- ePrivacy Directive 5(3) bars non-essential device access until consent. Using lookups, pixels, or SDK calls to decide whether to show a banner typically means pre-consent device access/communication, which is not “strictly necessary.”
- GDPR simultaneously governs any personal data you process in doing so (e.g., IPs for geo-lookup, telemetry identifiers): you need a processor agreement, and - if applicable - international transfer safeguards. If you skip any of those, you’re non-compliant even before your analytics or ads try to load.
“But we only need to show consent banners in Europe, right?”
No. Here’s the reality in 2025:
- Vietnam: PDPD (Decree 13/2023) requires express consent before processing personal data - cookies that identify or profile users fall in scope. The new PDPL (Personal Data Protection Law) will go into effect from January 2026, adding additional regulatory requirements and risks for non compliance, including a $120,000 USD fine for non-compliance as well as 5% of annual revenue.
- South Korea: PIPA and enforcement policy around behavioral advertising require user consent for cookies/online tracking that identify behavior.
- India: DPDP Act 2023 is consent-first; cookies that process personal data need freely given, informed opt-in.
- Thailand: PDPA + PDPC guidelines expect consent for non-essential cookies/trackers.
- Indonesia: PDP Law (2022) is consent-based; controllers had to conform by Oct 17, 2024 - non-essential tracking requires opt-in.
- Turkey: The KVKK and cookie decisions make it explicit: non-essential cookies require explicit consent.
- Brazil: ANPD’s cookie guidance points to consent for non-essential cookies and recommends compliant banners and practices.
- Japan: APPI doesn’t name “cookies,” but consent is required when cookies are used to provide person-related information to third parties (e.g., ad tech).
- UK + Norway (EEA): PECR/UK GDPR and Norway’s updated e-com guidance require opt-in for non-essential cookies, aligned with EU standards.
Add the entire EU/EEA (27 EU states + Iceland, Liechtenstein, Norway) and you begin to see the pattern: opt-in is the global norm for non-essential device access.
“And where jurisdictions don’t mandate opt-in, regulators now require automatic respect for opt-out signals.”
Why vendors keep getting this wrong
Because it’s easier (and cheaper) to simulate compliance than to enforce it. Many setups still load Tag Managers and third-party scripts before consent, then rely on banner clicks to signal preferences after device access has already occurred. That’s not compliant with ePrivacy Directive 5(3) - and regulators are catching up.
On top, classifying everything as “essential” is not a legal strategy. Technically required cookies (e.g., session/auth/security strictly required to deliver the user-requested page) never needed consent - but analytics, pixels, telemetry, CMP beacons, and marketing SDKs do. Calling a third-party CMP IP gate-fencing or loading telemetry for invoicing “necessary” doesn’t make it so.
The global split: opt-in vs opt-out
Plenty of jurisdictions outside Europe run opt-out regimes for sale/share or targeted advertising, especially across U.S. state laws. That is not a free pass to ignore consent. In fact, opt-out regimes now demand technical respect for universal signals:
Common requirements in opt-out regimes (outline)
- Honor Global Privacy Control (GPC) / approved Universal Opt-Out Mechanisms automatically (California and Colorado explicitly enforce).
- Provide “Do Not Sell/Share” and targeted-ads opt-outs (e.g., CPRA, CPA, VCDPA).
- Obtain opt-in for sensitive data in many states (e.g., CPA/CDPA categories), separate from cookie rules.
- Don’t dark-pattern the choice; keep it easy, prominent, and persistent (regulator guidance and enforcement trends).
- UOOM names and formats vary by state, but honoring them is automatic.
If you serve multiple markets, the safest baseline remains: do not access the device with non-essential tech until the user says yes - and always respect U.S. opt-out signals.
“Geo-IP gating isn’t compliance - it’s extra tracking to decide whether to show compliance.”
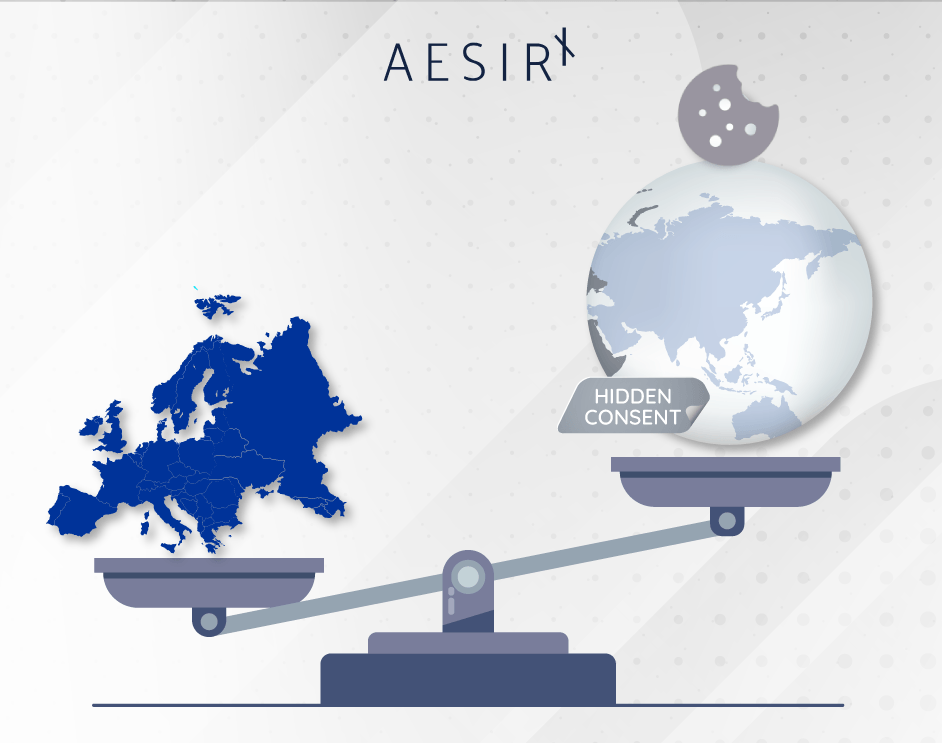
The uncomfortable truth about geo-IP gating
When a CCaaS hides the banner for visitors outside Europe by collecting and sharing IP addresses to geolocate, it creates new tracking that’s not strictly necessary for the user’s request. That alone is a red flag under the ePrivacy Directive (device access before consent) and a GDPR problem (personal-data processing) rolled into one. Worse, the publisher - not the vendor - usually carries the legal risk as the controller.
Legally, ePrivacy Directive 5(3) is triggered by any read/write before choice - including geo-IP gate-fencing calls and CMP “consent-as-a-service” telemetry for invoicing/usage - because these typically set/read identifiers or ping third-party endpoints. Separately, GDPR applies wherever personal data is involved (IP addresses, cookie/SDK IDs), which is the norm for analytics beacons, tag managers in preload, session-replay, fingerprinting helpers, and the telemetry itself.
Technically, geo-IP gating is brittle and noisy. Mobile carrier NATs, corporate VPNs, CDNs, and proxies make location inference unreliable, so users who need consent controls often never see them. You also increase data leakage: every call to a CCaaS endpoint shares IP + headers + timing - telemetry the user didn’t ask you to generate - just to decide whether to respect their rights.
Operationally, geo-gating fractures governance. You must track which markets got which banner, keep proof of when/why the IP was shared, and maintain region-specific records in your ROPA/records of processing. If the CCaaS sits outside the EEA, add transfer impact assessments and SCCs to your to-do list. It’s a lot of compliance debt for a feature that undermines trust.
Do it right instead:
- Show consent controls globally. Don’t hinge legality on location guesses.
- Block all non-essential tech by default; activate only after an explicit “yes.”
- If you truly need regional variants (languages, legal text), let users self-select region or derive it from on-device settings (e.g., Accept-Language) without third-party lookups, and without loading non-essential scripts.
- Keep consent and analytics first-party, minimize third-party calls, and store an audit trail of what loaded pre-/post-consent.
Put simply: geo-IP gating isn’t just compliance theatre - it adds legal exposure, reduces reliability, and erodes user trust. The next section shows what “good” looks like without the risk.
Countries requiring opt-in consent for non-essential cookies/device access (as of Oct 15, 2025)
Note: This list focuses on clear, affirmative opt-in for non-essential tracking/device access. It includes EU/EEA members and key jurisdictions with aligned requirements or authoritative guidance. Always verify sectoral rules and updates for your use case.
- EU/EEA (all 30 countries) under ePrivacy Directive 5(3) + GDPR (opt-in for non-essential).
- United Kingdom (PECR + UK GDPR).
- Norway (EEA; reinforced e-com guidance).
- Vietnam (PDPD + coming PDPL).
- South Korea (PIPA; behavioral advertising policy).
- India (DPDP Act 2023).
- Thailand (PDPA + PDPC guidance).
- Indonesia (PDP Law 27/2022).
- Turkey (KVKK cookie decisions).
- Brazil (ANPD cookie guidance).
- Japan (APPI - consent when cookies become person-related information for third-party provision).
This list is not exhaustive; several other jurisdictions either require opt-in or impose equivalent pre-consent controls for tracking technologies. Laws evolve - when in doubt, implement a global “consent-before-access” posture.
From theatre to enforcement
- Stop tracking before consent. Ensure Tag Managers, analytics, pixels, session replay, and CMP beacons are all blocked until a clear “Accept” exists. (ePrivacy Directive 5(3) applies to any device access, not just cookies.)
- Ditch geo-IP gating. Show the appropriate banner to every market that requires it - and stop sharing IPs with third-party CCaaS for “detection.” (IP = personal data; the user didn’t request this.)
- Make “technically required” honest. Keep only session/auth/security in the exempt bucket. Move analytics, pixels, telemetry, and CMP-vendor trackers out of “essential.”
- Respect U.S. opt-out signals. Honor GPC and state-level universal signals automatically. Provide prominent “Do Not Sell/Share” and targeted-ad opt-outs.
- Go first-party. Host consent and analytics first-party to minimize third-party sharing, improve accuracy, and build trust. (The first-party route is the direction regulators and guidance are nudging toward.)
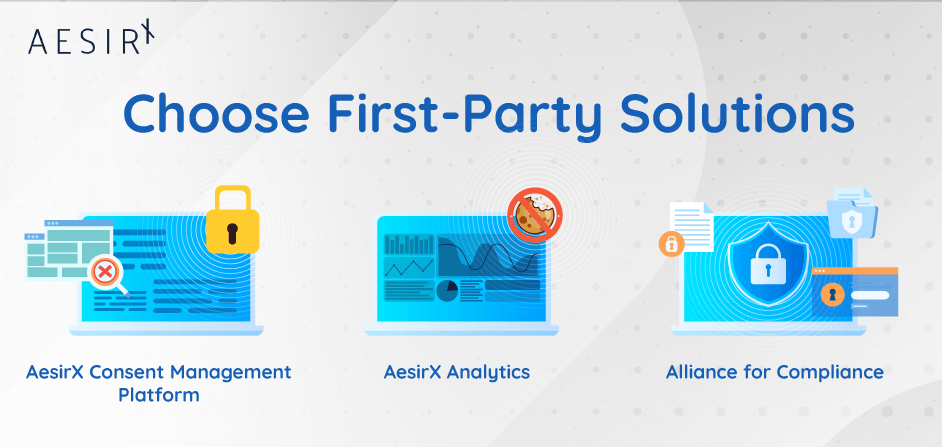
A first-party path you can implement today
If you’re tired of consent theatre, shift to a first-party stack that actually enforces the law:
→ AesirX CMP: loads from your domain, pre-consent blocking of all non-essential tech, double-action scanning (before/after consent), and an audit-ready trail.
→ AesirX Analytics: first-party, cookie-free analytics that only activates after consent, with the reporting you need - no fingerprinting.
→ Alliance for Compliance: managed monitoring + enforcement so your team doesn’t have to chase GTM or plugin regressions manually.
“This is safer. simpler, more honest - and it works across Europe, Asia, and the Americas without geo-gating or loopholes.”
Trust doesn’t have borders
When a website decides privacy only matters for Europeans, everyone else hears - loudly - your rights matter less. That isn’t a brand any of us want. And it’s not only opt-in jurisdictions (EU/EEA, UK, Vietnam, South Korea) that expect real controls before tracking; in the U.S., opt-out regimes now require sites to automatically honor universal signals - no dark patterns, no “EU-only” compliance theater.
California has enforced the Global Privacy Control (GPC) since at least 2022 - starting with the Sephora action for failing to honor user-enabled global privacy controls. In 2025, California’s privacy regulator issued its first CPPA enforcement order - a six-figure penalty against Honda that, among other issues, called out flawed cookie choice design and opt-out frictions. The message was unmistakable: symmetry and respect for user choices are mandatory.
Colorado likewise requires honoring a Universal Opt-Out Mechanism, explicitly recognizing GPC as its approved method under the CPA. And California just raised the bar again: AB 566 (“Opt Me Out Act”) will require browsers operating in California to provide a built-in opt-out preference signal - making compliance partly a protocol-level responsibility by Jan 1, 2027 (with CPPA rulemaking to follow).
So, Ignorance or Arrogance? It doesn’t matter anymore. Fix it.
- Make consent visible wherever opt-in is required; block non-essential tracking until “yes.”
- In opt-out states, auto-honor GPC/UOOM and eliminate asymmetry or friction in choices.
- Build on a first-party model - no geo-gating, no hidden telemetry, no pre-consent pixels - so users in Hamburg, Ho Chi Minh City, and Houston get the same respect by default.
Trust doesn’t have borders - and neither should your compliance.
Ronni K. Gothard Christiansen
Technical Privacy Engineer & CEO, AesirX.io
Check your site the simple way
AesirX Privacy Scanner (free) runs an automated privacy audit, flags cookies/pixels/third-party scripts that fire before consent, assigns a Low / Medium / High risk score, and gives you a downloadable PDF report with technical findings and fixes.
How to use it (takes a minute):
- Enter your URL and start the scan.
- Get the results page with your compliance risks summarized.
- Download the PDF and share it with your team/agency. (The free version allows 1 scan per domain per 24 hours; upgrade to AesirX Real-Time Scanner for unlimited, on-demand scans.)
What it checks
- Unauthorized cookies, pixels, HTTP beacons, third-party scripts loading pre-consent.
- Device access and data flows using the EDPS Inspection Tool + EasyPrivacy lists.
- A clear risk score (Low/Medium/High) so you know what to fix first.
If you want ongoing coverage
Consider AesirX Privacy Monitoring for scheduled scans (daily/weekly/monthly) with emailed reports - and on-chain logging for an auditable trail and as documentation of ongoing compliance efforts.
Next step after the scan
Use the report to block all non-essential tech until consent, switch where possible to first-party tools (CMP + analytics), and re-scan to confirm the fix.