Identity verification is now essential for everyday tasks, like opening a bank account or logging into social media. Traditionally, centralized systems handle this by storing personal data on servers, which can be vulnerable to security breaches. But with the rise of decentralized identity verification systems (DIDs), there’s a more secure, private, and user-controlled way to manage identities.
In this blog, we’ll explore what decentralized identity verification systems are, why they can be better than centralized ones, and how they’re shaping the future of digital identity.

What is a Decentralized Identity Verification System?
A decentralized identity verification system allows individuals to manage and verify their personal information without relying on a single, central authority. Instead of storing sensitive data on centralized servers, these systems use blockchain technology and cryptographic methods to protect the privacy and security of user information.
In decentralized identity systems, users create and control their own digital identities on a decentralized network. When identity (or ID) verification is needed, users can share only the necessary information with third parties, keeping control over what is shared, with whom, and for how long.
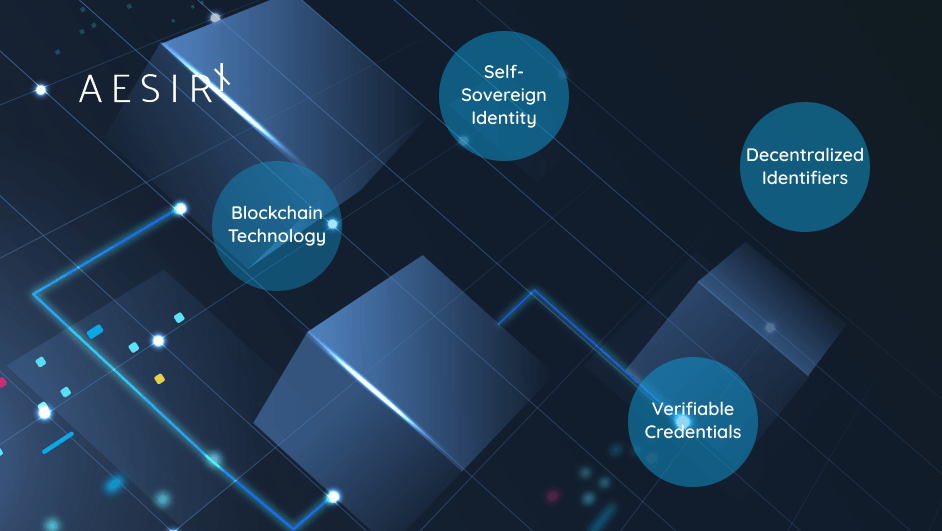
Key Components of a Decentralized Identity System
⮕ Self-Sovereign Identity (SSI): Individuals have full control over their identity data, deciding what to share, when, and with whom, without needing a third party to manage information.
⮕ Blockchain Technology: Acting as a secure digital ledger, blockchain keeps identity transactions safe and transparent. This setup minimizes risks like data breaches and unauthorized access by removing the need for a centralized database.
⮕ Decentralized Identifiers (DIDs): Unique digital identifiers that allow users to manage different aspects of their identity across various platforms.
⮕ Verifiable Credentials: Instead of sharing everything, users provide proof of only what’s needed, like confirming age or job title, without giving away more personal details than necessary. It’s about sharing just enough to get things done safely.
Centralized Identity Systems: The Current Standard
In a centralized identity system, personal data is stored and controlled by a single organization - whether it’s a government, a company, or an online platform. When you sign up for a service, your information is saved in a database managed by that organization. While this setup simplifies logging in and accessing services, it also comes with serious risks and drawbacks:
- Single point of failure: If the organization’s database is hacked or breached, large amounts of sensitive data can be exposed.
- Privacy concerns: Users don’t always have control over how their data is shared or used. In some cases, it can be sold to third parties without their knowledge or consent.
- Limited user control: Individuals must rely on these organizations to keep their data safe, with little insight into how it’s stored or protected.
Why Choose Decentralized Identity Over Centralized?
Decentralized identity offers several benefits that improve upon the weaknesses of traditional centralized systems.
1. Enhanced Privacy
With decentralized identity, users can share only the information needed to prove their identity. For instance, you can verify your age without revealing your full birthdate. This method, known as zero-knowledge proof (ZKP), guarantees that only essential data is shared.
2. User Control and Ownership
Decentralized systems give users full control over their data. Individuals manage their own identities using private keys, meaning no central authority can change or misuse their information.
3. Security and Lower Risk of Data Breaches
Decentralized systems, especially those using blockchain, are more secure. There’s no single database for hackers to target, reducing the risk of data breaches since information isn’t stored in one place.
4. Interoperability Across Platforms
Decentralized identity allows users to manage a single identity across various platforms. This means you can log in to different websites using the same credentials, making access easier.
5. Trust and Transparency
Blockchain technology provides transparency. All identity-related transactions are recorded on a public ledger, making them easy to verify and secure against tampering.
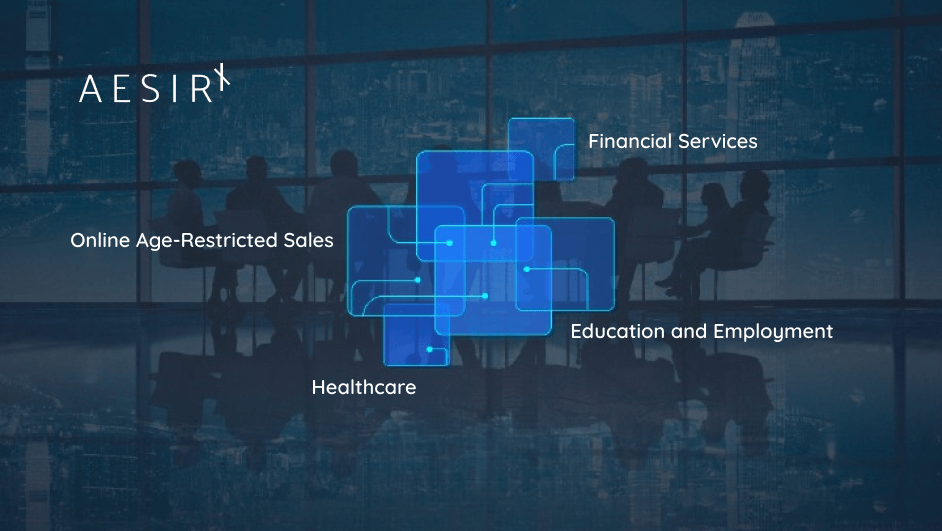
Real-World Use Cases of Decentralized Identity
- Online Age-Restricted Sales: Customers can verify their age for alcohol or tobacco purchases without sharing extra personal information.
- Financial Services: Users can verify their identity with banks without repeatedly submitting sensitive documents.
- Healthcare: Patients can securely share medical records with providers, minimizing the risk of data breaches.
- Education and Employment: Individuals can present verified credentials to employers, simplifying hiring without extensive background checks.
The Future of Secure, User-Centric Identity with AesirX
Decentralized identity verification systems are changing how we manage personal data, addressing growing concerns about privacy and security. As these solutions become more popular, individuals, businesses, and governments are realizing their value.
AesirX Shield of Privacy is a prime example, offering a secure and user-controlled way to verify identity while protecting personal information. Powered by the Concordium blockchain, AesirX Shield of Privacy provides an effective decentralized identity verification system with key features:
|
Decentralized Consent | Users control their data, sharing only what they choose, protecting privacy and maintaining regulatory compliance. |
|
Simplified Secure Access | Enjoy seamless login across Web2 and Web3 platforms with a single secure sign on - no more multiple passwords. |
|
Age & Residency Verification | Validate online interactions to align with users’ age and residency, promoting a trusted community. |
|
Seamless Integration | Easily integrates with popular CMS tools and connects with blockchain wallets like Concordium, MetaMask and BraveWallet for added security. |
Learn how to strengthen your online security and privacy. Sign up for AesirX Shield of Privacy today and take control of your decentralized identity!