By conducting a thorough Data Protection Analysis, you can quickly identify issues and proactively address them, achieving compliance and strengthening trust with customers, partners, and employees.
In this blog, we’ll outline the key steps, tools, and techniques for effective Data Protection Analysis and show how AesirX solutions can make this process easier and more efficient.
Understanding Data Protection Analysis
What: A Data Protection Analysis identifies, evaluates, and strengthens the safeguards your organization uses to protect sensitive information. It involves pinpointing potential vulnerabilities, assessing the effectiveness of existing controls, and designing new measures to secure personal data. This analysis often includes regular risk assessments, policy reviews, and testing data security practices, all aimed at preventing unauthorized access and data breaches.
Why: Protecting personal data not only aligns with privacy laws but also builds trust and loyalty with users. A data breach can lead to severe consequences, including regulatory penalties, legal repercussions, and a damaged reputation. Furthermore, a proactive approach to data protection helps organizations adapt quickly to emerging threats and continuously improve their security posture.
Who: This analysis is typically conducted by data protection officers or compliance teams, but website managers, customer agents, and other team members can also contribute by assessing risks, implementing controls, and monitoring systems. Expanding this responsibility across roles reinforces efforts to guard against unauthorized access and data loss.
How: This analysis typically follows a structured approach that includes:
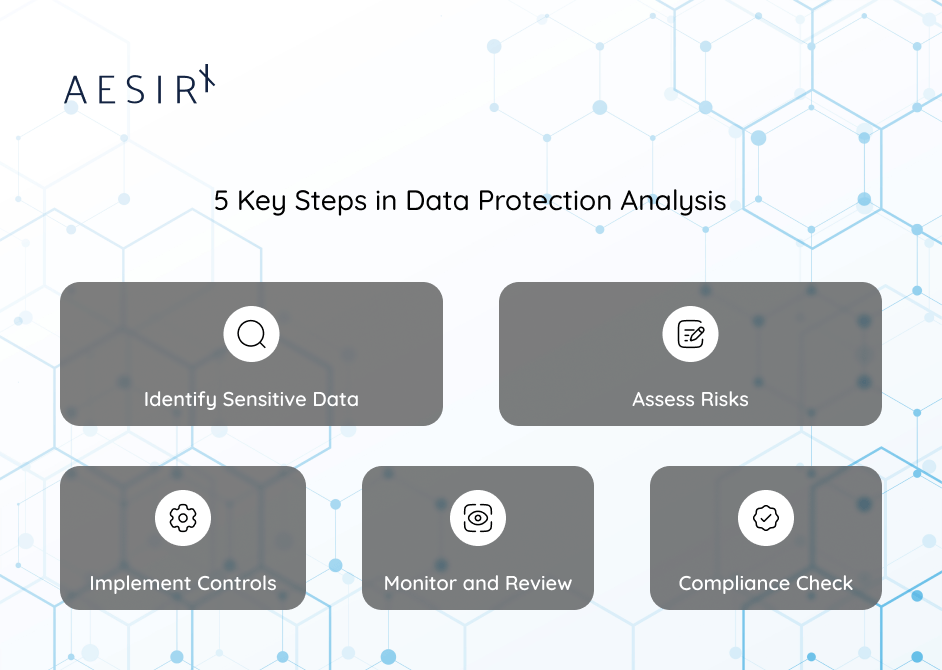
Key Steps in Data Protection Analysis
1. Identify Sensitive Data
⮕ Identify all sensitive data your organization handles, from personal data (names, contact information) to financial records (banking details, transaction histories) and intellectual property (patents, trade secrets).
⮕ Additionally, consider where this data is stored, whether on local servers or cloud platforms, and the countries in which your data resides, as these factors can affect your compliance with regulations like GDPR and the ePrivacy Directive.
Understanding what data you have, where it’s stored, and how it may be shared is essential for effectively protecting it.
2. Assess Risks
⮕ Next, conduct a Data Privacy Risk Assessment to identify threats to your data, including who has access or unauthorized access, what third-party trackers are running on your website, and any missing user consent.
⮕ Third-party trackers can expose data to outside access, and collecting data without consent risks non-compliance with data protection laws.
By evaluating the likelihood and impact of these risks, you can prioritize protective efforts where they’re needed most.
3. Implement Controls
⮕ Using your Data Privacy Risk Assessment, implement specific protections to address vulnerabilities. These can include encryption, access controls, data masking, consent mechanisms, data anonymization, pseudonymization, and regular security audits.
⮕ You can also use techniques like Single Sign On (SSO) with zero-knowledge proofs (ZKPs) and decentralized identifiers (DIDs).
Strengthening these controls helps protect sensitive data from unauthorized access and ensures compliance with privacy requirements.
4. Monitor and Review
⮕ Regularly monitor Data Protection Measures to verify they’re effective. Automated tools can track access, detect unusual activity, and generate alerts for potential threats.
Regularly reviewing your strategies helps address new risks and improve defenses.
5. Compliance Check
⮕ Make sure your data protection practices meet the requirements of GDPR, CCPA, ePrivacy Directive, or other relevant regulations.
Frequent audits and assessments will verify compliance and help you adapt to changing data protection laws.
AesirX Tools for Data Protection Analysis
AesirX offers a range of solutions to streamline data protection, including the AesirX Privacy Scanner, Privacy Review, Privacy Monitoring, and First-Party Foundation.
AesirX solutions offer privacy scanning and reviews, continuous monitoring, and compliance assistance tools. These tools assist in meeting GDPR, CCPA, and ePrivacy Directive requirements by conducting privacy checks and continuous monitoring.
| AesirX Privacy Scanner | AesirX Privacy Scanner offers a site evaluation on GDPR compliance and identifies privacy concerns. This free tool provides a clear report on areas needing improvement and helps establish a baseline for data protection. |
| AesirX Privacy Advisor AI | This AI-powered tool interprets your Privacy Scanner results, providing actionable insights and recommendations tailored to your organization’s needs. It simplifies the steps for enhancing your privacy and security practices. |
| AesirX Privacy Review | The AesirX Privacy Review examines privacy practices and offers improvement recommendations. Delivering actionable insights and strategic recommendations, this review advances your data protection approach, aligning it for compliance and optimizing efficiency and security. |
| AesirX Privacy Monitoring Service | This continuous monitoring service checks your website’s privacy practices for compliance. Real-time alerts help you proactively address issues, providing ongoing protection and adherence to data protection standards. |
| AesirX First-Party Foundation |
AesirX First-Party Foundation focuses on consent management and ensuring compliance. It includes an Analytics & CMP that helps organizations collect and manage user data while maintaining compliance. The Business Intelligence tool turns data into valuable insights for better decision-making. The Shield of Privacy applies pseudonymization to protect sensitive information and improves user control and transparency over their data. Finally, the First-Party Server provides secure data storage, reducing risks from third-party sharing. |
Techniques for Effective Data Protection Analysis
- Data Mapping: Map how data moves through your organization, from collection to processing, storage, and sharing. This process helps identify vulnerable areas and protects all data flows.
- Regular Audits and Assessments: Conduct regular, automated privacy audits to measure the effectiveness of your protections. Identifying gaps helps you strengthen defenses and adapt to new security challenges.
- Employee Training: Educate employees on data protection best practices. Regular training helps ensure that everyone understands their role in maintaining data security and compliance.
- Incident Response Planning: Develop a response plan for potential data breaches. This plan should outline the steps to take if a breach occurs, including containment, investigation, and stakeholder communication.
- Continuous Improvement: Data protection is an ongoing process. Regularly evaluate and improve your protections to stay ahead of new threats and utilize the latest security advancements.
Strengthening Your Data Protection Strategy
Conducting an effective Data Protection Analysis helps protect sensitive information and build trust with your stakeholders. By following these steps and utilizing AesirX’s tools, you can improve your organization’s data protection strategy and remain compliant with data privacy regulations. Remember, data protection is a continuous commitment to security, compliance, and trust.
Start with AesirX Privacy Scanner to assess your compliance today. Enter your URL here for a free analysis of your website’s data privacy status.